Crypt(?)
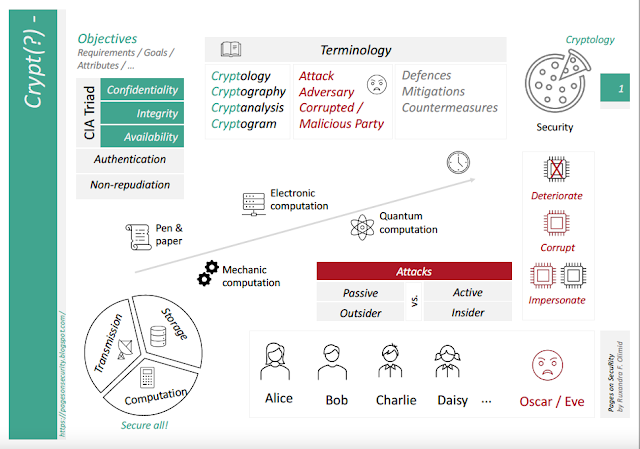
| Cryptology is one part of the much larger domain of (information) security. Think of the information security field as a pizza 😃 Then cryptology is just a slice of it. |  |
Cryptology evolved continuously in time: it started with techniques that only used pen and paper, went through the era of mechanic computation, and nowadays uses electronic computing at a large scale. Today, an active research direction is post-quantum cryptology, which considers quantum computation too. An interesting (but long!) well-known book about the history of cryptology is David Kahn's book The Codebreakers: The Comprehensive History of Secret Communication from Ancient Times to the Internet. Another newer, shorter book on cryptology for the large public is The Code Book by Simon Singh.
%202.png) | As in any field, there are some (fundamental) notions you need to become familiar with from the beginning. First, there are the "crypt-" words, such as crypt-ology, crypt-ography, crypt-analysis, etc. |
Cryptology contains both cryptography and cryptanalysis, where cryptography is the (mathematical) discipline that studies techniques, methods, constructions, etc. to provide information security, and cryptanalysis is the study of (mathematical) techniques used to break information security. There exist other crypto- words such as, e.g., crypt-ogram that denotes an encrypted text (I will explain encryption in a later post), usually given as a puzzle to solve.
The above definitions are informal (I will often avoid rigorous definitions). For definitions, I recommend two resources: one is the Encyclopedia of Cryptography and Security, and the other is the NIST CSRC Glossary.
Security should (to some extent, as perfect security is not a realistic goal) stand against adversaries that mount attacks. Corrupted entities or malicious parties are good examples of such adversaries. Defences, mitigation techniques, countermeasures, etc., help to achieve security. Moreover, information security must be considered regardless the state of the data: in transmission, during storage, and at computation/processing. Of course, there is not much point to securing a client-server communication (secure data in transit) if the server itself is unprotected (do not secure data during storage). The McCumber cube is a model that asks to secure information in all three states. |
In the literature, the adversary is normally called Oscar or Eve. Similarly, the involved parties are named Alice, Bob, Charlie, etc. The naming started with a fundamental paper in cryptology, which introduced RSA (I will explain RSA in a different post, later on). Alice & Bob - A History of The World’s Most Famous Cryptographic Couple nicely explains the story of Alice and Bob.
| Many times the types of adversaries and the attacks that they mount are interchangeable. For example, an insider mounts an insider attack while an outsider mounts an outsider attack. Insider and outsider refer to the relation of the attacker with the attacked target. To understand better, think of an organization. An attack mounted by an employee is a form of insider attack, while an attack mounted by a competitor organization (this should, of course, not happen!) is a form of an outsider attack. | .png) |
Adversaries and attacks can also be passive (when the adversary does not actively interfere in any way but only "listens") or active (when the adversary actively intervenes, e.g., by injecting or deleting some data). Again, this is a simplistic way of seeing adversaries and attacks - other criteria to classify adversaries and attacks (e.g., adaptive vs. non-adaptive adversaries) and more fined steps (e.g., semi-passive or semi-active adversaries) do exist.
 |
The actions an adversary can take to fulfill his/her goal(s) are numerous and various. In relation to a target (e.g., a piece of hardware/software, a station, a network), I believe these can be put into three main categories: (1) deteriorate: the adversary harms the target in a way to stop its normal functioning or slow it down (e.g., flood a network to perform Denial-of-Service (DoS)), (2) corrupt: the adversary gets control over a party (e.g., install malware on a computer to steal information), and (3) impersonate: the adversary pretends to be someone else (e.g., masquerade a legitimate party such as a bank to steal sensitive data). |
| The CIA Triad gives the three most common objectives of security: (1) Confidentiality, (2) Integrity, and (3) Availability. (1) Confidentiality means that only legitimate parties can read/understand the data. Think, for example, of a bank that wants to protect the personal data of its customers. Data must be stored encrypted (I will come back to encryption in another post) so that even if the adversary gets access to the encrypted files/database, he/she cannot decrypt to get the plain data. (2) Integrity means that non-legitimate parties cannot modify/change the data. Think, for example, about a money transfer. The transfer must be integrity-protected such that an adversary cannot change the amount of money transferred. (3) Availability means that a service/system/etc. is available for the legitimate parties. Think, for example, about the website of the bank. The website must be available for customers, and security should prevent an adversary from performing a DoS attack by flooding it with requests. |  |
In addition to the CIA triad, many other objectives exist. I only name here authentication and non-repudiation. To maintain the same scenario, an example of authentication is when the bank customers access their account via the web interface (probably by using a multiple-mode authentication involving their phone/token, etc.). Non-repudiation means that a party cannot deny an action he/she performed. Again, a simple example might be a customer that cannot deny he/she paid a bill and pretend the paid amount of money back to his/her account.






Comments
Post a Comment